- Executive Offense
- Posts
- 🔴 Executive Offense Issue #3
🔴 Executive Offense Issue #3
A blow to the darkweb, SCA, Burp Madness, LOLBINS, ASM, ++
EO is a security newsletter that focuses on the intersection between offensive security and security strategy. Sometimes hacker-ish, sometimes CISO-ish. Very blazer over the t-shirt type of vibe…

Genesis Market taken down in “Operation Cookie Monster”
Holy smokes, this is a big one! If you're not aware of what Genesis Market is, then you might have been living in a hole for the last five years. Genesis Market is one of the premier underground dark web markets for selling credentials and cookies that are stolen from your employees. For years, they made this process as easy as shopping on eBay. They were the one-stop shop for adversaries who didn't want to do their own mass phishing campaigns. They were a second-tier market where password dumps from breaches ended up. And in their private forums, they also offered brokered introductions between threat actors, spammers, phishers, and all kinds of other bad guys.
This week, law enforcement from around the world worked together to dunk on these bad guys (did you get it? Because you dunk a cookie?). This is a real win for internet safety and for the end user. Cited in the tweet below is the fact that Troy Hunt's Have I Been Pwned offers a search function to see if your information was in the market. So make sure you and your loved ones are not in that one.
Just blogged: Seized Genesis Market Data is Now Searchable in Have I Been Pwned, Courtesy of the FBI and "Operation Cookie Monster"
— Troy Hunt (@troyhunt)
1:43 PM • Apr 5, 2023
The crackdown has some unintended side effects, like making threat intel for various companies much harder for a short period of time. There still exist six or seven other smaller dark web forums that traffic in credentials and cookies, and I'm pretty sure a successor to Genesis Market will appear inside of two or three months, just as always happens with these darknet markets. For any of you threat Intel folks out there, Russian Market seems like the incumbent at the moment.
Sponsors
I am actively looking for sponsors. Reach out to [email protected] for more information

Static Code Analysis
This week, I want to broach the topic of SCA (Static Code Analysis) tools. Before becoming the seasoned security practitioner and leader I am now, I worked alongside an SCA company. At that time, there were really only three players of any consequence in the industry. Now, there are just shy of 20.
So, which one do you pick? And what should you look for in an SCA vendor? Fortunately, my friend Abhay created a quick, TikTok-style post discussing the top considerations when selecting an SCA tool:
Think you're secure? Think again!
SAST tools are a crucial part of any security strategy, but they're not foolproof.
Stay ahead of the game and learn how to optimize your scans with these expert tips from @abhaybhargav! 🔒🔍
#SAST#tools#devsecops#appsec#applicationsecurity
— AppSecEngineer (@AppSecEngineer)
4:31 PM • Apr 5, 2023
On the topic of SCA tools, I want to build on Abhay's excellent outline and share a few other things that I value.
Firstly, an SCA tool by itself does not provide all the value. I believe that an SCA tool is part of a larger ecosystem of secure development. This includes not only scanning the code, but also remediating the code, and learning how to avoid making similar errors again. Sometimes, this involves education, gamification, e-learning, and other approaches.
So, when I evaluate an SCA vendor, I not only want to make sure they meet the criteria outlined in the video, but I also want to know what they are doing to support me other areas. Let's break it down:
Language Support and Effectiveness (see how large their rules library is)
Incremental Scanning
Customize SCA Rules
Supplementary developer education or documentation
Innovation
You’ll notice the last listed item there is innovation. I want to see that my SCA tools research arm is actively conducting quality research (not just generating new code packs). That's why I bookmarked this tweet this week about utilizing GPT-4 for code analysis:
We put GPT-4 in Semgrep to point out false positives & fix code. http
— ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ (@DanielMiessler)
10:58 PM • Apr 4, 2023
This is absolutely wild. We will continue to see giant leaps forward for defense in the next six to nine months due to the availability of AI. It doesn't really matter which side of the fence you're on when it comes to the intelligence of AI and LLVMs—what GPT-4 and LLVMs are going to do that is valuable is aggregating every single piece of defense data that an analyst can't go through in a year, in seconds.
P.S. If you want to dive into the deep, dark world of static analysis, GitHub released an excellent blog post this week that offers great insights.
If you're even more of a deep diver, one of my fellow bug hunters, Space Raccoon, wrote an excellent blog on CodeQL and SemGrep rule writing.
Lastly, in March, I wrote what is probably one of the most comprehensive threads on secure coding resources from around the Internet that are free. I listed over 12 resources for developers or offensive security professionals to level up their understanding of code. If you're unable to obtain a SCA tool that offers you a deep level of education or resources, you can certainly supplement with these:
💪 Code Literacy is a Super Power for Hackers 💪
(and Security Literacy is a super power for devs)
Knowing how vulnerabilities are mitigated makes you a 10x engineer (sec or dev)
Check out this thread for some of my fav
🔥FREE🔥
resources. ⬇️
(Also send me more!)
— Jason Haddix (@Jhaddix)
10:15 PM • Mar 3, 2023
Sponsors
I am actively looking for sponsors. Reach out to [email protected] for more information

This week is jam-packed with offensive security topics. In fact, there are so many that I considered splitting this issue into two, but we're just going to try to roll with it.
All the LOLs
We're going to kick it off today with all of the LOLs. Of course, by LOLs I mean Living Off The Land Binaries, or if you expand the term, Living Off The Land Binary, Scripts, and Libraries. In offensive security, LOLBins are legitimate executables, processes, scripts, libraries, or tools that are natively available on a targeted operating system. As an offensive security professional, mostly during red teaming, you can use these for initial compromise, persistence, evasion, lateral movement, or data exfiltration.
The best online resource to get a solid understanding of *Bins is:
(Windows) https://lolbas-project.github.io/
(*nix) https://gtfobins.github.io/
This week, though, we have some additional projects to bolster this type of TTP. Lol Drivers is a new project to consolidate vulnerable and malicious drivers to streamline research and analysis for offensive security professionals.
Introducing the Living Off The Land Drivers (LOLDrivers) project, a crucial resource that consolidates vulnerable and malicious drivers in one place to streamline research and analysis.
loldrivers.io
LOLDrivers enhances awareness of driver-related security risks and… twitter.com/i/web/status/1…
— The Haag™ (@M_haggis)
2:56 PM • Apr 5, 2023
The project categorizes a plethora of third-party drivers that exist from various vendors, including some that are shipped or installed in prebuilt computers from motherboard manufacturers, graphics card companies, system fan software providers, or makers of keyboards and mice. It's a fascinating project that expands offensive capabilities into these areas. Each driver comes with a link and a snippet of information about what it can accomplish.
Coming soon, we also have a project for LOOBins, Living Off The Orchard Bins. These are Mac-specific LOLBins that will be published once the project reaches a certain level of maturity!
LOOBins... coming soon! I'm looking for some help. If you're a macOS security expert who would like to contribute to a mac-specific variant of #lolbas#gtfobins please get in touch.
— Brendan Chamberlain (@infosecb)
2:35 AM • Apr 5, 2023
So, what's the defensive angle for this offensive TTP? Well, it really goes back to some old staples, such as:
Leveraging the Principle of Least Privilege: Implement the principle of least privilege on user accounts within the operating system. Restrict users' access and permissions to only what is necessary for their job roles. This can reduce the risk of *some* attacks.
Application Whitelisting: In some cases, using application whitelisting can prevent the execution of unauthorized or malicious programs, including LOLBins, under certain circumstances.
EDR Software: Robust EDR software can recognize, through heuristics, the outcome of the utilization of a LOLBin. Make sure you bring it up in your next vendor bakeoff!
Burp Suite Plugins
Now let's move on to everyone's favorite interception proxy, Burp Suite. This week, there were several different threads outlining people's favorite extensions for Burp. Some of these are tried and true, and I definitely keep them in my arsenal, while others were certainly new to me. Here are a few of the threads where users jumped in to discuss the extensibility of application security's most beloved tool:
I took the liberty of consolidation all these for you. You can find them all on the bAPP site.
H1 Report Finder
WordPress Scanner
Pentest Mapper
Autowasp
Burp Bug Finder
Auth Analyzer
Active Scan++
NoSQL Scanner
Nuclei Burp Integration
Wordlist Extractor
AuthMatrix
Backslash Powered Scanner
Collaborator Everywhere
SAML Raider
Autorize
Param Miner
Retire.js
Turbolist3r
Deserialization Scanner
Header Editor
IP Rotate
During my bug hunting/ endeavors, there are a few extensions that I particularly appreciate.
One of them is called "Gap". This Burp extension employs sophisticated logic to extract endpoints and parameters from HTML and JavaScript.
And two, is a NEW one on the market that i’m REALLY excited about. Burp-VPS-proxy! This extension simplifies the process of setting up new proxies that provide you with a fresh IP for web testing. In the past, managing this required a somewhat complex socks proxy configuration. Now, it can be controlled directly through your VPS API and the Burp extension. Say goodbye to being blocked by Cloudflare or Akamai, as you can effortlessly spin up a new IP!
Attack Surface Management
Attack surface management is a rapidly growing industry, with new vendors emerging every day. I have a specific hot take on this sector - it was all born out of open-source code and bug bounty hunters. Although scraping the internet for assets isn't a particularly new concept, the tools for doing so gained popularity during the early years of bug bounty programs. Before that, most security testers either didn't focus on a holistic attack surface or relied on brute force as their primary method of enumerating subdomains.
Nowadays, attack surface management can encompass a range of tasks, such as discovering new domains, subdomains, exposed code, SaaS-related assets, and providing a visibility layer for all this data. Several vendors have even extended their services beyond “surface management” to include vulnerability scanning.
So, what can you do if you don't have the budget for a high-end external attack surface management vendor?
Since this field originated from open-source code and bug bounty hunters, it's relatively easy to set up simple solutions yourself. The first core feature of external attack surface management is finding domains and subdomains. You'll want to not only locate these assets but also scan them regularly to be notified of any new ones that emerge. Then, you need to decide how to handle that data.
I find it quite amusing that attack surface management vendors invest heavily in their dashboards and graphs. Most people using an attack surface management vendor will eventually export the results from that fancy GUI to a more practical format like CSV. This enables them to import the asset data into their CMDB or manage the project with a spreadsheet. What project, you ask? Well, the project could be an asset register or, for some, a risk register.
Fortunately, you can accomplish this with one simple tool - OWASP's Amass.
Simply install and run OWASP Amass on a box and run it on a cron job every two days (this is what I do).
Here’s the simple workflow:
Amass Enum every two days on a cron job
Amass Track after every run. Send this output to a Slack or Discord channel using Project Discovery’s Notify
To tell you the truth I wanted to go into a deeper dive on how to actually set this up but, this week's edition is getting too long to fit that in so I might do it as an addendum issue coming up with a special guest.
For now enjoy two of the best guides on Amass out there by Hakluke and Dan Miessler:
Context Aware Content Discovery
I'm not sure how this one slipped past me, considering that I view myself as something of an expert in content discovery.
If you're not familiar with the concept, content discovery is the phase of a web application security test where you enumerate all potential endpoints, parameters, and files that may exist on the web server or application. Since many offensive security assessments operate without full knowledge of the target (i.e., not in a "clear box" manner), this enumeration often involves brute-forcing items using various tools and lists. This process can result in a significant amount of web traffic being directed at the target server, sometimes to the displeasure of the site owners. To mitigate this strain, you can identify the technology used by the site and then only use brute force lists that are relevant to that technology, thereby reducing the number of requests.
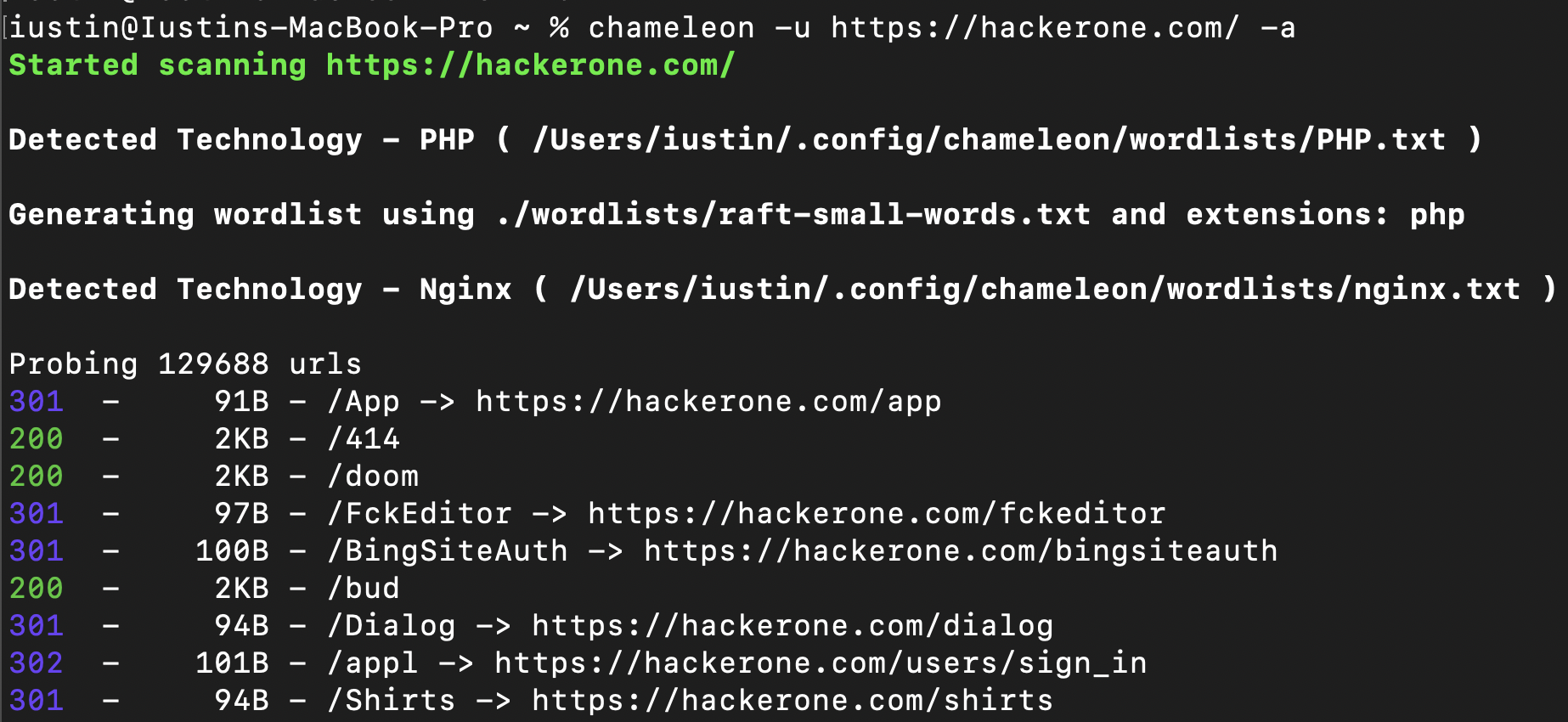
Last September, a hacker by the name of Youstin released a tool capable of context-aware content discovery. The general idea is that, with just a few initial requests, the tool can identify the technologies in use and then automatically load specific lists for those technologies that you have stored on your file system.
The tool, named "Chameleon," offers enough customizability to add new fingerprints and set different lists according to your preference. While I typically conduct content discovery using tools like ffuf or ferobuster, Chameleon introduces a great workflow and feature set. For a complete overview, check out the full blog post from last September on Chameleon, the context-aware content discovery tool.

Alright, we've certainly exceeded the typical word count for a newsletter, but I'm committed to ensuring that the content provided to you all meets my high standards for depth and quality. We still have a few topics left for this week, including red team and bug bounty evasion techniques, as well as scaling and cloud red teaming and testing. Rest assured, I'll be covering these topics in next week's newsletter. So, stay tuned!
Thanks for reading. I sincerely appreciate it. If you enjoyed the newsletter, please share the signup page on Twitter or with friends!
If you are a red teamer or bug hunter, consider checking out my training in July:
📢 I have decided to give my live training, once, again this year.
Come join me in July for two days of the:
🎯 The Bug Hunter's Methodology Live 🎯
Will be dropping the registration link this weekend.
tbhmlive.com
— Jason Haddix (@Jhaddix)
3:34 PM • Mar 17, 2023
And finally, if you are anywhere near Florida, come hang with me and several of my hacker buddies at HackSpaceCon!