- Executive Offense
- Posts
- 🔴 Executive Offense Issue #5
🔴 Executive Offense Issue #5
short but sweet :)
EO is a security newsletter that focuses on the intersection between offensive security and security strategy. Sometimes hacker-ish, sometimes CISO-ish. Very blazer over the t-shirt type of vibe…
Welcome everybody to Issue 5 of Executive Offense!
You're receiving a somewhat late release because this past week, I was out at B-Sides San Francisco and RSA Conference. While I fully intended to deliver a jam-packed issue a few days after the con, I fell ill with COVID. Alas, on to this week's newsletter!

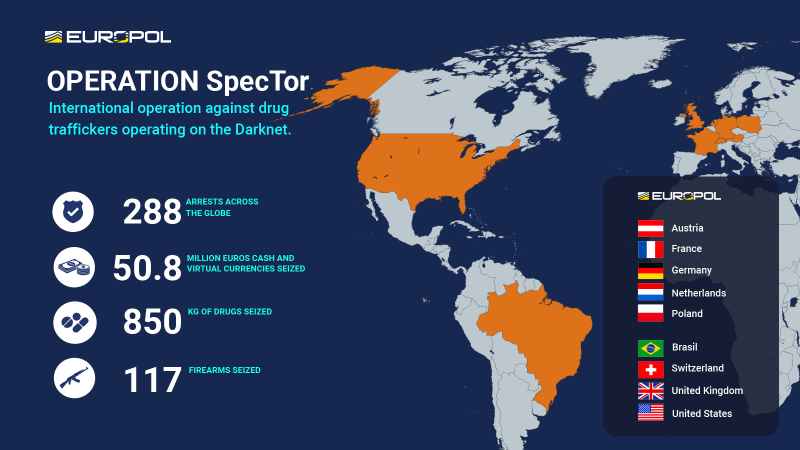
Operation SpecTor
This week in the news, I want to highlight two big busts that came out of the international law enforcement community. The first was Operation SpecTor, run by Europol in conjunction with several other law enforcement agencies. This operation busted 288 drug dealers across the globe and seized over 850 kilograms of drugs.
This bust was a bit polarizing in the tech communities across Reddit, Twitter, Telegram, and Discord. Some say it was a major win or and others said could be making things worse. On one hand, some argue that the darknet marketplaces for drugs offer a safer experience to those seeking out narcotics. Some postulate that the drug trade is cleaner and safer with the efficiency and community policing in the dark web trade. On the other hand, drugs are illegal, and no matter if it's digital or physical, the community around drug sales is not just isolated and is often tied to other types of crime.
Another bust was made by the FBI this week when they seized nine cryptocurrency exchanges that were facilitating money laundering for ransomware actors. This one is pretty cut and dry, as the nine exchanges were explicitly engaged in laundering money for some of the biggest ransomware operators on the internet.
One thing that draws me towards these news stories of these operations is my personal experience being on both sides of them. If you want to hear more about that, you can listen to a small part of my origin story on Darknet Diaries.
Sponsors
I am actively looking for sponsors. Reach out to [email protected] for more information

Easy Peasy Persistence…
This week's topic in the Blue Pill section is indeed blue in nature, but if you're an Red Teamer, it might give you some inspiration as well.
I wanted to highlight a talk I had the pleasure of watching by Ryan Thompson from CactusCon this year. Ryan's talk was called "A Peek Inside an Adversary's Toolkit."
The talk goes over some very simple and effective means of command and control (or at the very least, persistence).
These techniques involves utilizing common applications for remote assistance or remote PC control.
Specifically, Ryan covers AnyDesk and Ngrok in his presentation but also lists out several alternatives. Ryan goes over these applications, what you can achieve with them as a malicious actor, and how to hide them from a normal user.
The reason these applications can be used for more sticky persistence is:
They are often whitelisted as legitimate user apps by your endpoint protection.
Nothing about them shows up as malicious, including their binary signatures.
They often operate using HTTP and HTTPS looking like web traffic.
One reason I love this presentation was because I've used these apps in the past on red team campaigns. Not only have I used them in my offensive security work, I've also seen them be used against me as a defender as secondary or backup persistence for various threat actors. I also had the unique pleasure of working for GoToMyPC early in my career, unwittingly teaching me how a proper C2 should work 🤣
I highly suggest you watch the whole talk because there's more in it than just a breakdown of these apps… but for defenders out there often you wanna be on the lookout for these applications:
AnyDesk
LogMeIn / GoToMyPC / GoToAssist
TeamViewer
ConnectWise
Zoho Assist
TightVNC
Chrome Remote Desktop
Ngrok
How do you defend?
While each of these software applications works a bit differently, some utilize specific protocols over specific ports that you can block on the egress. Others are not so straightforward, as mentioned before, and they can tunnel traffic over HTTP and HTTPS. In this case, as Ryan points out in his talk, many times to facilitate the tunneling, they use a standard DNS server which you can black hole. You can also implement application whitelisting against these applications.
The problem is, there’s a lot of alternatives just in the “tunneling” category like Ngrok. See: https://github.com/anderspitman/awesome-tunneling
Ultimately, staying ahead of these TTPs require a proactive and multifaceted approach. The above at a wholistic level, and then periodic hunting and auditing of software in your environment.
Sponsors
Reach out to [email protected] for more information

Shodan all the things
This week on the red side I loved this piece of content by my friend Ben (NahamSec):
Utilizing Shodan during an engagement is epic passive data source.
Ben goes though using ShodanCLI to pull a bunch of passive recon data from a target!
In addition, I did a thread a while back on the best Shodan resources for offensive security people. There is that summarized for you all 😃

Official Shodan Documentation:
Data reference: https://datapedia.shodan.io/
List of search filters: https://www.shodan.io/search/filters
Query syntax: https://help.shodan.io/the-basics/search-query-fundamentals
Official Examples: https://www.shodan.io/search/examples
The Shodan Pentesting Guide:
https://community.turgensec.com/shodan-pentesting-guide/
Cert.sh and Shodan Recon with @GodfatherOrwa
https://www.youtube.com/watch?v=YoXM4m1VEM0
Shodan Filters and Hacks
https://www.youtube.com/watch?v=GyZFM5IaH2Y
100 Shodan Queries for Discovery
Org filter dorks for technologies
General other interesting queries

Well friends, that’s about all the writing energy I have for today. I’ll be recovering from the rona this week and back to full strength next week.
Next week will be heavy on industry insights from RSA as I have a TON of notes I took.
Stay Safe!
If you are a red teamer or bug hunter, consider checking out my training in July!