- Executive Offense
- Posts
- 🔴 Executive Offense Issue #6
🔴 Executive Offense Issue #6
Passwords, RSA, Internal threats, ransomware controls +++
EO is a security newsletter that focuses on the intersection between offensive security and security strategy. Sometimes hacker-ish, sometimes CISO-ish. Very blazer over the t-shirt type of vibe…
Welcome everybody to another wonderful week of Executive Offense! My name is Jason Haddix, and I'll be guiding you through a week's worth of news, analysis, and random thoughts coming straight out of my head!
Now that I'm freshly recovered from last week, let's jump right into it with some news!

🥂 A Passwordless future
Over the last couple weeks there's been a bunch of posts about the future of authentication. We've discussed in previous episodes of Executive Offense that FIDO/2 keys are the way to go and are especially valuable to protect your organization from the giant threat of phishing. One of the notable articles that came out over the last few weeks is Google's “So long passwords, thanks for all the phish”:
This article outlines one of the major pushes in a company like Google to adopt a passwordless future, moving more towards FIDO keys or things that you own in the authentication workflows.
One point to bear in mind is that while I look forward to a world where I no longer have to remember passwords, it is also important to understand that this doesn't completely mitigate the phishing problem.
While many forms of phishing currently attack users to steal their credentials with man-in-the-middle type capture forms (which this protects against), other types of phishing target installing malware onto your users' computers.
☣️ If a user becomes a victim to credential-stealer malware that can access the browser's cookie store, as discussed in previous issues of Executive Offense, they could still bypass authentication using a current cookie from the browser.
What's important to keep in mind is the adaptive nature of threat actors, as reflected in the constant evolution of Tactics, Techniques, and Procedures (TTPs). When one technique gets exposed, attackers tend to switch to other techniques. We remain optimistic that the move toward passwordless authentication and the use of FIDO keys will compel attackers to abandon the relatively easier approach of capturing credentials via fake web popups. By doing so, we hope to push them towards what seems to be a more challenging task—trying to infect the underlying machine.
The idea here is to make their malicious endeavors increasingly difficult, time-consuming, and less profitable.
🤠 The Big Bad RSA Roundup
As I promised, I wanted to provide a recap of the RSA conference for 2023. While the event did expose me to the dreaded coronavirus, I can't blame it, because it also opened my eyes in several ways.
While I was preparing this extensive RSA roundup, a colleague and whom I greatly respect, Anton Chuvakin, wrote his own version of an article like this. To be honest, Anton and I share many of the same conclusions.
But here’s some extra anyways 😉
The Industry and Recession
RSA was bigger than ever this year. The booths were more elaborate, there were plenty of new vendors entering the market, and you couldn't really tell that we were approaching what most people predict to be a substantial recession.
Now, this could be because preparation for the conference begins six months to a year in advance. It might also imply that the current climate might be less dire than we realize, and that cybersecurity will continue to enjoy generous funding from the venture capitalist (VC) cabal.

I've conversed with multiple peers about the current times and how the market is playing out. Some say that funding is drying up and it's becoming more difficult for security startups, while others have no problem at all securing funding.
Personally, I believe the reality lies somewhere in the middle. Over the next year and perhaps by the next RSA, things will tighten down by about 15-20%, but in the grand scheme of cybersecurity, that isn't much, and many startups will continue receiving generous funding offers from VCs and acquirement proposals from larger companies.
Cloud Security
Now, the second subtopic under the big, bad RSA roundup is something I began to notice while walking up and down all 8 billion miles of the RSA show floor…
Cloud is Hard
I can't tell you how many vendors I saw that specifically existed to help you secure or configure your cloud environments because the innate technology and controls that come with them are too hard for most people to understand.
I observed countless vendors whose primary purpose was to provide an intuitive user interface over an unintuitive one or apply some automation to help you secure some of the most basic things in cloud security.
On the more complex side, some of them did attempt to grapple with intricate problems like Identity and Access Management (IAM) across fleets of users and managing not to fall asleep while trying to parse logs from all the different sources of cloud logs.
While all of this is a noble pursuit, it makes me wonder, why can't the cloud vendors fix this? It's their platform, and as users of these platforms, we should demand more intuitive and easy workflows in the realm of cloud security.
AI and Big Orgs
While I expected to see a bunch of vendors tout AI and ML features in their products, it didn't quite pan out as I anticipated. I observed numerous talks by big companies announcing their rapid adoption of AI, specifically Large Language Models (LLMs), and their ability to quickly parse massive amounts of data. However, there were very few actual demonstrations. Everyone seems to agree on the dream that someday, the Security Operations Center (SOC) Level 1 will be replaced by a magical talking robot, but no one has achieved it yet, and many are still far from it.
In cybersecurity, the complexity of building a system like this relies on the ability to collect all the data for AI to execute upon. As an industry, we're still working on this problem and will be for the next couple of years. While some people may want to sell you the dream of a talking robot, very few are actually incorporating AI technology into their products.
However, I did see a few novel ways to apply AI to different products. I was particularly impressed with some of the integrations in the Data Loss Prevention (DLP) space. These integrations illustrate how LLMs can vastly improve our understanding of a document's context and classify it accordingly in a DLP setting.
One point that became apparent is that companies possessing massive datasets pertaining to security problem spaces are poised to benefit the most, embodying the "rich get richer" sentiment. A prime example is Veracode's announcement of AI utilization in analyzing applications, scanning, and contextualizing secure coding. Veracode has over a decade of scan data, secure coding knowledge, and metadata regarding such problem spaces, making them prime candidates to be among the first to capitalize on AI. This pattern could extend to every vendor across various security product genres.
This weeks Executive Offensive Newsletter is brought to you by:
Hands-on Full-stack Security Training for Security Engineers
Learn Cloud Security, Kubernetes, DevSecOps, and more. 100% hands-on.
We guide security engineers, architects, and developers to get new skills in AppSec with over 1000+ interactive and hands-on labs. Get 10% off with code “HADDIX10“

So, what's on the menu for blue teamers this week?
📘 The Top Red Team Internal Findings
First off is Andy Gill (who I'm a huge fan of, by the way) who posted on LARES Security's Top Five Insider Threat Findings:
Now, this post isn't one of those bloated, aggregated, and often unuseful types of articles. This is a real, respected red team that conducts genuine internal campaigns, contextually breaking down their most successful TTPs.
The thing that struck me when reading this article was that, indeed, these are absolutely the ways that internal campaigns unfold, both from running them myself at BuddoBot, and from being on the receiving end of real adversaries using these techniques against some of the companies where I've been a security leader.
This article is chock-full of information that will enable you to detect different methods, both through strategy and technical means. As with most blue team information, if you're a red teamer, many of the tools in here can also be parsed for a better understanding of how blue teamers will attempt to root you out and to comprehend the automation you can apply for each of these findings.
Please enjoy this article; it's an excellent read, and Andy is one of the best people in the field. Also there is a webinar at the end of the article!
🛞 The Ransomware Control Matrix
So what keeps us up at night as security leaders? It's ransomware, of course!
It's very easy to get bogged down in deciding which controls to apply to address this specific threat. You find yourself faced with a plethora of both macro and micro-level security strategies to apply, as well as specific protection products. Many of these decisions can weigh heavily on your budget and the allocation of your team. Bearing all this in mind, a friend of mine recently introduced me to the Ransomware Control Matrix.

The RCX is a series of cascading sets of security controls that you can implement to avoid or mitigate the impact of ransomware. It offers an easy-to-navigate checklist so that you can see exactly where you stand for each of the levels of readiness. There are 3 levels of readiness in the matrix: foundational, advanced, and elite.
Using this cascading style of readiness checklists allows you to prioritize your security program to be more resilient against the threat of ransomware. The framework also aligns with other industry frameworks such as NIST, MITRE ATT&CK, and MITRE D3FEND.
I highly recommend checking it out and integrating it into discussions about how you structure your security program and allocate your budget for the upcoming fiscal year. Start with addressing the gaps in the foundational level and then move up the ladder as you begin to check off all the relevant boxes for your organization.
📣 Disclosure Done Right
This week, Dragos Security suffered a cybersecurity event where a malicious actor attempted to connect and pivot to their internal network during the onboarding of a new employee.
Now there are a couple of interesting aspects to this. One is the scenario. It's not clear from the disclosure if the employee was targeted because the attacker group knew they were going to work for Dragos, or if they had been compromised for a long time and an opportunistic attacker group decided to capitalize on this user going to this employer.
Either way, during the onboarding process, many companies do not officially control the IT assets of the prospective employee. This means there is a short window in which a compromised employee might connect to various parts of your infrastructure without your regular security controls.
Now, I'm here to tell you that there are a lot of security experts out there claiming this would never happen to them because their onboarding is immaculate, but most of them are lying. I know for a fact that a majority of the Fortune 100 companies I've consulted with have really poor practices when it comes to employee onboarding, and that this attack is absolutely possible for a short window of time until the employee switches to a managed device. The saving grace in Dragos' case was the implementation of excellent role-based access control (RBAC).
There was a lot of conjecture online on additional processes to defend against this specific scenario, but many of them fall apart when you work at an organization with more than 100 people. To be honest, I wish I had a silver bullet to offer here, but I'll have to mull this one over for a bit longer…
The second part of this article that was a breath of fresh air was how open Dragos was about their event and the level of detail they provided to inform the public. Their associated blog post about the incident included both adversarial and defensive timelines and an ample amount of information about how they handled the issue internally. The crazy thing is that I'm pretty sure Dragos received more good PR than bad from this security incident 🤣
Sponsor
Adversaries are growing in sophistication. Attack frequency and complexity is increasing. Do you rely heavily on automated tools and vulnerability scans to validate your security and readiness? Automated scanning and occasional testing won’t keep up and can’t match the creativity of a targeted attack by an actual malicious actor. The only way to know if your organization can be breached by malicious hackers is to bring on a team of professional hackers, like BuddoBot, that are Built to Breach™.

To be honest, my red team fam, I should probably split all this content into a couple of newsletters… but sometimes I really don't listen to my content creation peers and I do what I want! Buckle up, because we've got a lot to go over this week.
🔍️ Acquisition Recon
The first thing I wanted to discuss is a new recon technique that I've added to my bug hunting and red team methodology, which involves a thorough examination of organizations' acquisitions and investments. Usually, I would use Crunchbase for this kind of thing, but if you want to think in video game terms, Crunchbase is level 1 and alepth.OCCRP.org is level 5.
First off, Crunchbase and many other acquisition sites are paid business information aggregators, so their free accounts only go so far in providing acquisition details for your target.
This new method relies on a source called OCCRP Aleph. I know it's an odd name, but OCCRP Aleph is a global archive of research material for investigative reporting. They keep track of 414 million public entities and parse over 252 discrete datasets in more than 141 countries.
Here's how to use it for reconnaissance, red teaming, and bug bounty.
Head over to the site, register, and then search on the main page for your target company (in this case, Tesla Motors).

Step 1
Once the search is complete, find the entry that comes up, closely related to your company and associated with the dataset "US SEC CorpWatch."

Step 2
You might have to click around on a couple of these datasets until you find one with a substantial list of assets and shares, as pictured below:

Step 3
Upon clicking on "assets and shares", you'll be given a list of all your target's investments and acquisitions.

Step 4
Using this method on on a site, I've discovered some fascinating, small, and seldom-mentioned acquisitions and companies tied to targets in both my bounty work and my red team work. Happy hacking!
🛠️ Keep up to date with Offsec Tooling
This one is bright but brief! Gwendal Le Coguic, a prominent tool author in the bug bounty and offensive security space, has built a portal to try and consolidate all your offensive security tooling needs in one place! Offsec.tools is a community-driven site where you can go to check out the latest offsec tools!
Each tool is categorized, so you can easily find them by category.
Normally, staying current in this field requires a lot of attention to Twitter and GitHub. As long as Gwendal's site continues to receive support from the community, we'll all have one convenient place to go for researching new tooling.
🗺️ Mindmapping your Recon Data
One of my students from RSA loved the idea of mind mapping your recon data, so they wrote a script that will take command line output from various tools and turn it into a mind map or markdown format.
The script organizes the data hierarchically, sorts it alphabetically, and also supports JSON output! This means you can effortlessly take your command line output and view it in markdown, plain text, Obsidian, or XMind with ease! Give it a try!
Two weeks ago I had the chance to learn new recon techniques from the great @Jhaddix at #RSAC2023 and now I have more domains than I can handle. I built a tool to organize and sort the data called Recon MindMap. It's #opensource and it's available at github.com/Alevsk/rmm
— Lenin Alevski | @[email protected] (@Alevsk)
7:19 AM • May 8, 2023
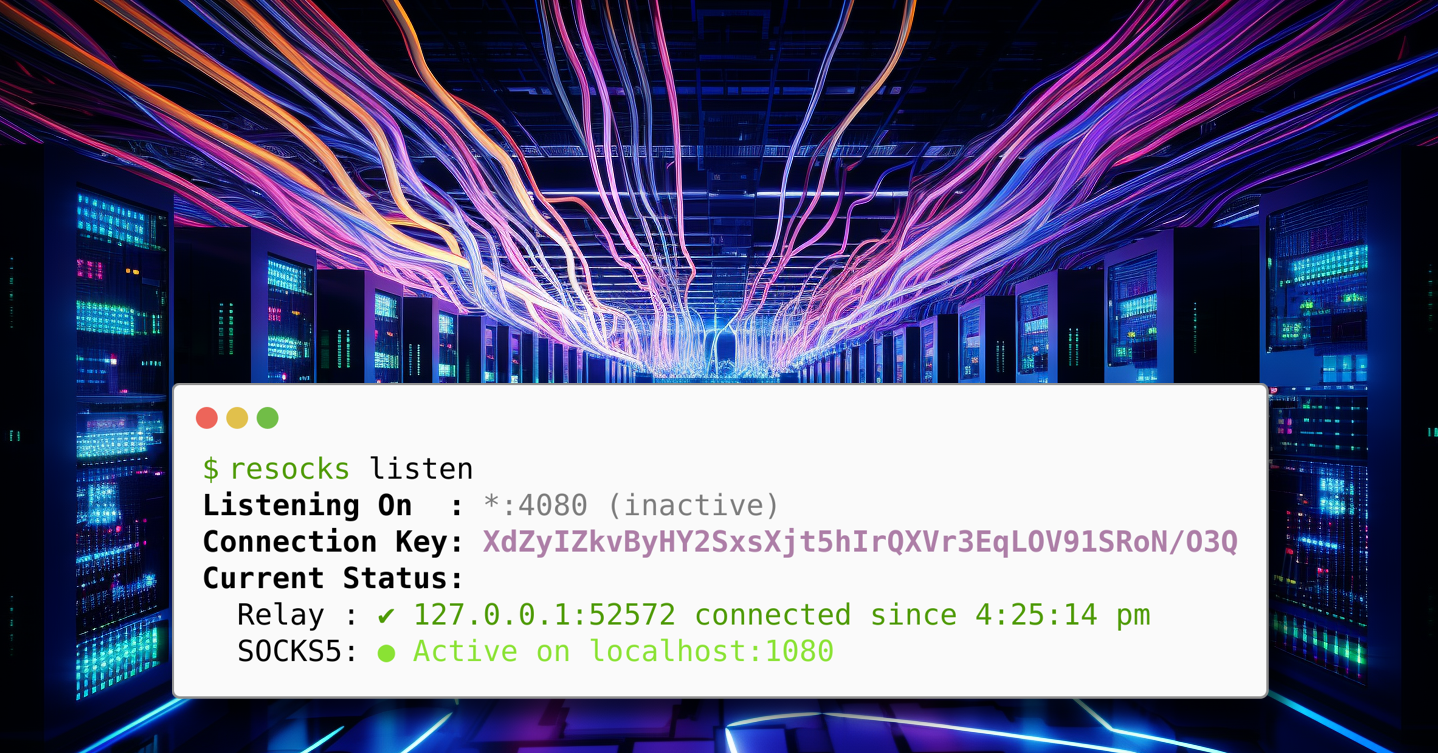
🐍 Stable and Secure Proxying for Red Teamers
If you've ever done any red teaming or penetration testing, you've likely had to proxy and pivot your way through a network. Often, this occurs through port forwarding or SSH, but these approaches can be somewhat cumbersome to set up and may have some security drawbacks during testing. Additionally, in an unstable network, if you lose one of these connections, it's challenging to resume where you left off.
Last week, redteam-pentesting.de released resocks, which addresses several of these concerns and includes a reconnect feature to retrieve your shells when needed!
The need and use cases for this tool are quite complex, so I couldn't cover them in the newsletter, but if you're a red teamer, you probably already understand what I'm talking about. Head over to the blog and read about this alternative to pivoting on internal hosts!

Well, fam, that's it for this week! Next week, I hope you're ready for a massive brain dump on all things AI hacking. Not only have I teamed up with the AI Village to help them organize some of their events, but I'm also on an absolute tear both building offensive security tools leveraging AI and learning how to test AI itself.
Next week's issue will be almost exclusively focused on this topic, and I'll be sharing everything I've gathered for you all to get ready for this emerging technology as offensive security specialists, security leaders, and defenders.
Stay Safe!
If you are a red teamer or bug hunter, consider checking out my training in July!